At the heart of every technology infrastructure and operation, lies the network.
Network Security protects your network and data from breaches, intrusions and other threats. This is a vast term that describes hardware, software and cloud solutions as well as processes or rules and configurations relating to network use, accessibility, and overall threat protection.
At the cornerstone of every security strategy, is the network.
We provide solutions and services to help you secure your network at every layer
Next Generation Firewalls
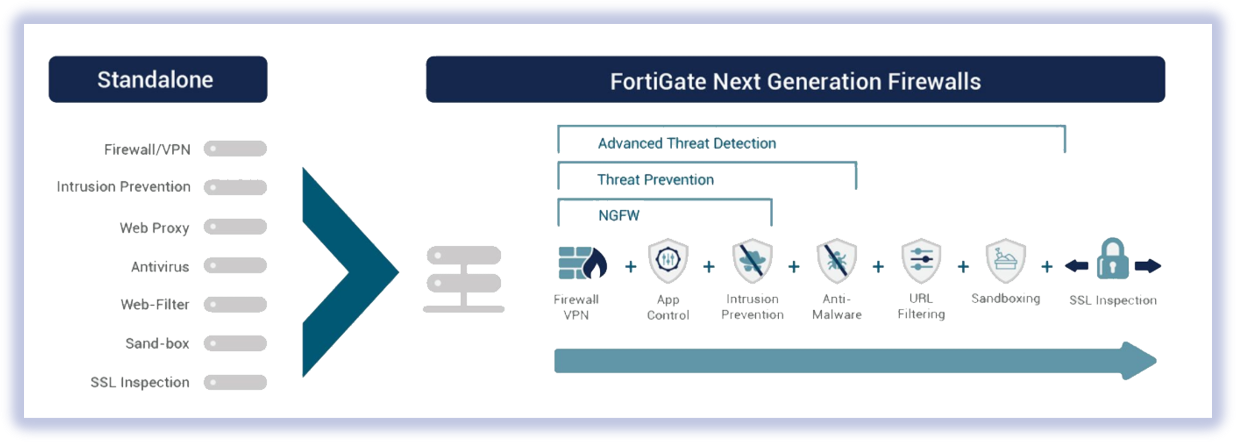
While a traditional firewall typically provides stateful inspection of incoming and outgoing network traffic, a next-generation firewall includes additional features like application awareness and control, integrated intrusion prevention, and cloud-delivered threat intelligence. Once you identify your requirements, we help you choose the right technology that suits your needs vs the most cost effective solution. Usually deployed with a number of advanced features such as Intrusion prevention (IDS/IPS), Web filtering, Data Loss Prevention and Email and anti virus protections for the most demanding set ups
Secure Network Architecture Services
A company’s network, whether on cloud, or on-prem, or both, presents the biggest attack surface, hence poses the greatest challenge to secure.
A combination of hardware, software, processes and configurations must be properly analysed, architected and inter woven into a seamless cross functional ecosystem, secured at multiple layers.
The scope can involve network devices, physical or virtual, servers, applications, logical designs, identity & access management (IAM), Wi-Fi networks and not just.
IAM & well segmented networks become even more important as the world moves towards the zero trust architecture model











